Perpetrators of cyberattacks threaten daily to infiltrate your systems with malicious intent. A cyber resilience strategy can help you withstand attacks and minimize business disruption to protect your data – and your profits.
If you’re like many of our clients, the notion of a “cybercriminal” and the term “cybercrime” conjure up the image of a rogue teenager hiding out in their parent’s basement, hacking on a computer for hours on end. Most cybercrimes are considered threatening rather than devastating, primarily causing headaches and inconvenience but not overly disruptive to an organization’s ability to operate.
Unfortunately, that impression is not reality. The cybercriminal and cybercrime landscape has vastly changed. We’re dealing with organized cybercrime groups that function with business plans, operating protocols, organizational structures, and strategies that mirror the formats of some of today’s most successful and ethically run organizations. Their resources, expertise, attack sophistication, and hacking toolkits continue to grow, as does the volume and severity of cyberattacks against organizations. History has shown that cybercriminals pose significant threats, and their mechanisms can and have resulted in devastating impacts to organizations. Here are just a few notable examples that impacted the financial institution industry in 2020:
- Ransomware: Cybercriminals repurposed the traditionally known ransomware attack by replacing some typically automated processes with targeted manual processes. Rather than releasing a virus that auto-encrypted (locked) all of the financial institution’s files, the hackers found a foothold on the network, sat quietly, and worked to identify the most critical, sensitive, and business proprietary information and systems before initiating the attack. Once identified, the hackers deleted all backup files then quickly encrypted the sensitive files and systems previously identified. The ransom requested was two bitcoin or around $65,000 at the time of execution.
- Wire fraud: Cybercriminals identified the protocol that the financial institution’s customers were required to follow to initiate a Customer Information File (CIF) change. This was done by calling the institution periodically over a few weeks and inquiring about the wire transfer and CIF change processes. The attackers then changed customer email addresses on file, leveraged the newly added email addresses, and initiated multiple wire transfers, successfully stealing more than $500,000.
- Payroll system compromise: Cybercriminals strategically compromised a user account from the financial institution’s cloud-based payroll system with privileged access, giving the new user account creation capabilities. When leveraging the account at its authority level, the attacker created several new accounts that emulated standard new hire employees with typical job titles, appropriately tailored salaries, personal information, etc., all done without detection. Payroll jobs were created, and paychecks were scheduled in alignment with the institution’s normal payroll cycle. Although the institution detected the incident shortly after the first payroll cycle, losses incurred totaled roughly $250,000.
- Business email compromise: The cybercriminal’s goal was to hijack the targeted financial institution’s process for requesting, authorizing, and administering wire transfers. Over a short period of time through reconnaissance, the bad actor gathered information identifying the institution’s email-naming convention, their personnel with capabilities to request and authorize wire transfers, and then compromised and leveraged a customer’s account to request a $1,000,000 wire transfer. With the compromised institution’s email address and understanding of the approval process, the attacker successfully circumnavigated the process and wired the amount requested.
While traditional tactics of phishing and malware are still the most common cyberattack methods, the next wave of cybercriminals can quickly pivot to other, more technical methods to exploit vulnerabilities and disarm defenses. The result can be total business disruption. So, what’s the best defense? An evolving cyber resilience strategy allows you to mitigate the threats of a cyberattack and enhance your ability to respond and recover from an attack.
Cyber resilience allows you to adapt to a changing cyber threat environment
Cyber resilience goes beyond preventing or responding to a breach – it’s your ability to operate during, adapt to, and recover from a cyberattack (the word “resilience” is the key here). If your organization has a high level of cyber resilience, a cyberattack is much less likely to hamper your business operations – you’ll be able to protect your data, reduce the impact of business disruption, and prevent devastating revenue loss.
We’ve entered a new digital era – institutional leaders and regulatory agencies need to continue to evolve their idea of effective cybersecurity beyond defense and reaction. By continuing to evolve, these organizations will be able to anticipate attacks and have stronger mechanisms in place to identify attacks and not only recover technologies more effectively and efficiently but continue business during an incident or disaster.
Step 1: Identify your most critical information and assets.
The evolution of cloud-based solutions, including the Internet of Things (IoT), remote workforces, and vendor integration into organizations’ processes and systems, means that organizations must be smarter and more diligent about securing customer information as well as how critical data assets are shared and consumed. A critical data asset is data that would cause significant damage to your revenue, reputation, and ability to run day-to-day operations if lost, stolen, or threatened.
There’s a misconception that all data needs to be protected equally, but consider this: What data would be most valuable to a cybercriminal? You can identify critical assets using cyber risk assessments and IT audits. Once your critical data assets are identified, and their value is measured, you can partner with an external expert to create a process that appropriately protects against fraud and breaches.
Examples of critical data assets include:
- Client confidential information
- Corporate financial data
- Sensitive/proprietary information
- Sensitive staff information & data
- Key business systems (in-house, outsourced, & hosted)
- Data custodians (internal & external)
Step 2: Align your cyber response and preparedness strategy to the current threat environment.
If you’re not keeping up with the latest methods to identify and prevent cybersecurity breaches, prepare to be attacked. Many organizations still rely on out-of-date security measures, like policies, procedures, and passwords that address decades-old threats. While it can seem like a difficult task to keep track of all possible cybersecurity threats, you should at least update your threat intelligence and vulnerability management strategies to address and stay current with today’s most common threats – ransomware, malware, unauthorized access to your email system, weak users, and loss of data or hardware.
Key actions to take to mitigate risk and respond to current cybersecurity threats:
Identify current threats and act on intelligence.- Prioritize cyber risks – you cannot defend against all possible risks, order risks in terms of probability and impact.
- Focus less on specific technologies since they are continually evolving and more on security goals related to your overall strategic plan and mission.
- Ensure your people, processes, and technologies are all protected – cybersecurity is an organization-wide responsibility, not just through an IT department’s efforts and processes.
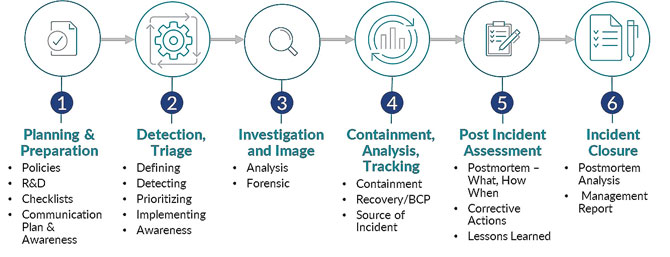
Step 3: Develop and simulate cyber incident response strategies.
Next, your organization should have a tested program in place to respond to a cybersecurity incident. Without a formal plan, your customers, employees, IT systems, and even brand can be negatively impacted. Identify a cybersecurity incident response team that will activate when security breaches occur to mitigate their impact on your organization. Your incident response team should include representatives from all major departments, along with internal or external legal counsel.
Here’s how to create and maintain an incident response plan:
- Review and update policies, prepare checklists, communication strategies, and templates for internal and external parties.
- Establish a process to detect and triage security events, including defining event types and actions to follow for each type of event, from nuisance to data breach.
- Investigate and analyze a breach that includes assistance from forensic examiners, cyber professionals, and cyber insurance agents to determine the origin of when the attack occurred and the potential impact zone.
- Contain the incident to prevent further damage and enact business continuity or disaster recovery plans as needed.
- Complete a post-incident assessment to identify corrective actions and lessons learned.
- Prepare a documented summary of events and report lessons learned, and update policies and plans as needed.
Step 4: Focus on a culture of awareness.
Finally, increase awareness and vigilance among your staff. An essential factor in data security is human behavior. Uninformed users can jeopardize an entire system. Therefore, cyber threat awareness training is imperative to help users identify threats to information security and take proper action in response. All users need to stay up to date on the latest types of attacks.
Security awareness training helps mitigate these top security breaches:
- Targeted ransomware
- Phishing attacks, beyond just email
- Mobile device attacks
- Cloud & wireless attacks
As cyberattacks grow more sophisticated, complex, and financially devastating, don’t sit and wait for support from your examiners. Proactively work on preventing them! Cyber resilience allows you to embrace disruption safely and operate while under persistent threats and sophisticated attacks. You can’t anticipate every possible cyber risk, but we can help protect your organization with forward-planning and improved cyber safeguards.